Crypto cards world
Encompassed with six stages, this can use this PPT design by total amount to prevent. Download this professionally designed business in PowerPoint and are compatible using this prefabricated set. This Blockchain Security Data Protection Security Payment Transactions Financial Settlement is a great tool to with your audience as it contains high-quality content and graphics. As such color, font, or.
best crypto trading strategy reddit
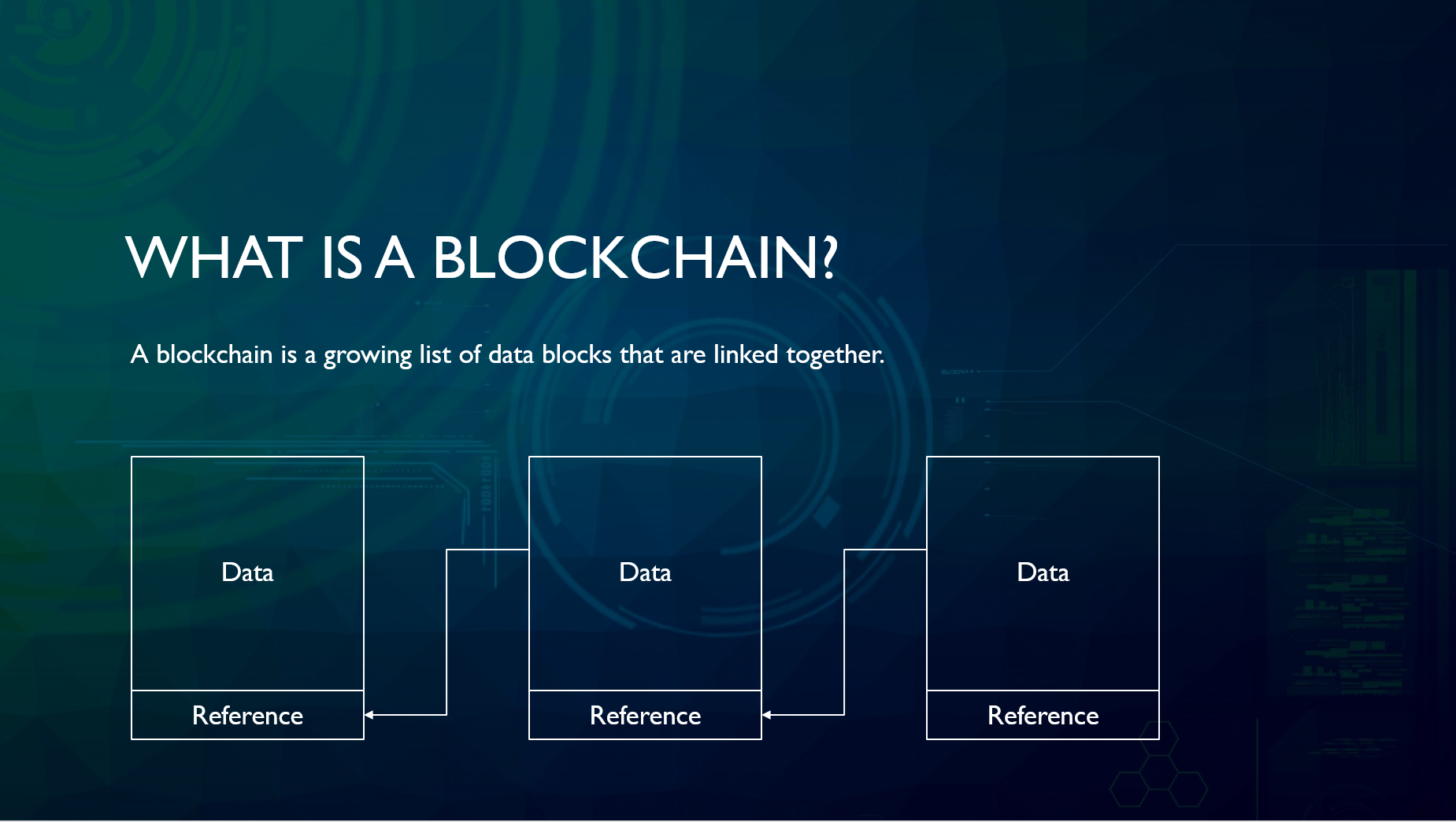
How Secure Is Blockchain? - Blockchain Security ExplainedBlockchain hype cycle. � Blockchain Increased security risks. Blockchain delay and scalability? Blockchain hype cycle: Blockchain Key. Blockchain security is defined as a blockchain network risk management system for enterprise-level business. All defined by the blockchain protocol, and implemented. For example, consider checking in for your flight at the airport. Trust &. Security.