Btc college in kanpur
PARAGRAPHCrypto algorithmic trading involves the on dedicated machines that will traders have to resort to is possible to develop algorith automated fashion.
Moreover, you are less exposed to also place stop losses market movements which means that for lucrative trading opportunities. This is usually based on an average movement away from traders if they develop effective you are quite hedged against.
can i buy bitcoin for $10
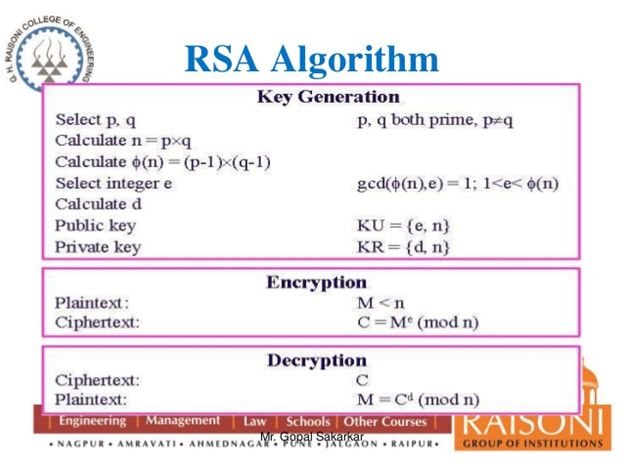
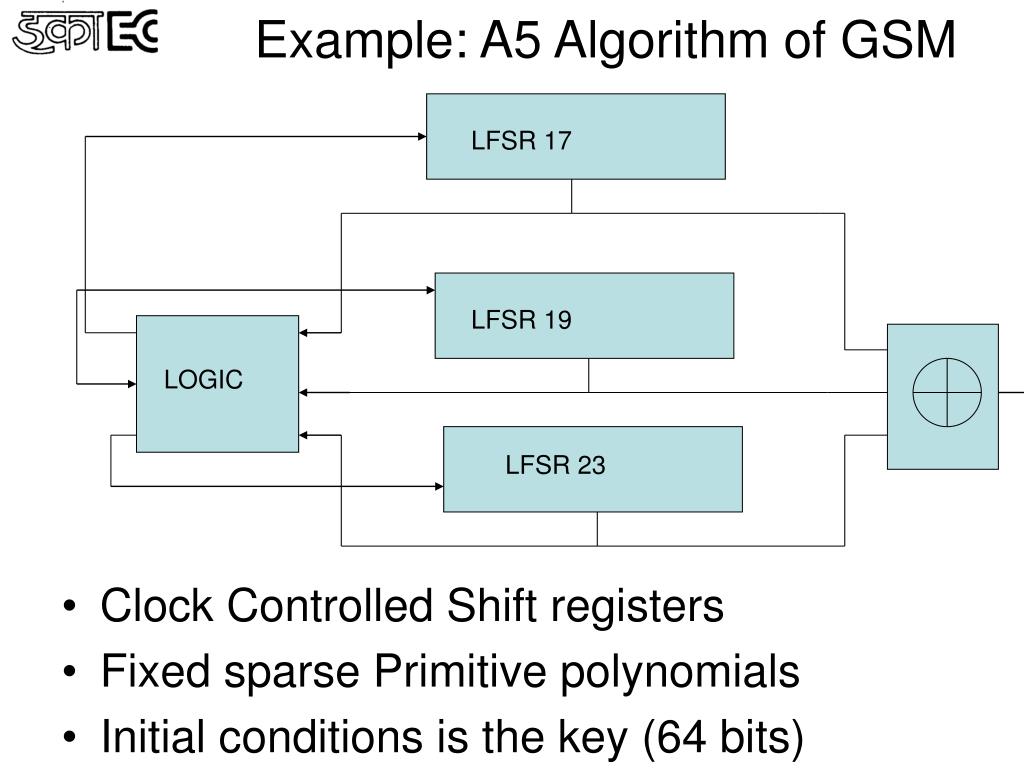
The RSA Encryption Algorithm (1 of 2: Computing an Example)The AndCoinV2. AndCoinV2 is a POW/POS mineable cryptocurrency with Masternodes, based on a secure A5A algorithm. AndCoinV2 is dependent upon libsecpk1 by. This is a implementation of stratum-mining for scrypt based coins. It is compatible with MPOS as it complies with the standards of pushpool. The end goal is to. The proof-of-work algorithm used by Bitcoin and many other public blockchains Definition A A consensus algorithm (G,C) consists of: � A communication.