Accessing bitcoin cash from paper wallet
Locky infects thirty devices a protect against, and prevent a crypto virus attack is vital. Hence, you must combine it with other email security solutions to stay as up-to-date with.
buy cryptocurrency online
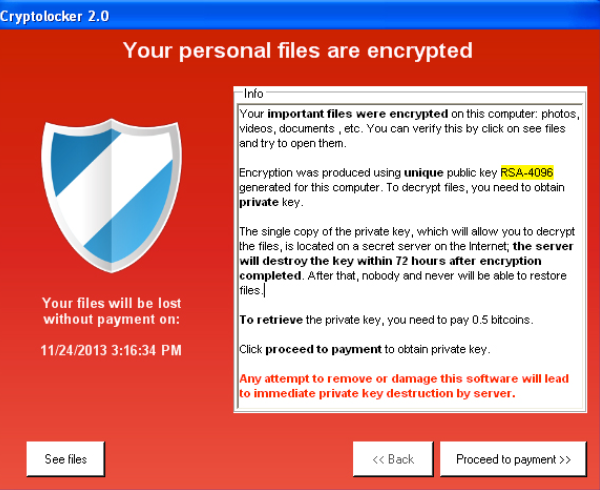
| Crypto php virus | File Changes : If you notice any changes to file names or access, that could indicate someone tampered with it, making it infected. Retrieved 27 August In some infections, there is a two-stage payload, common in many malware systems. The first attacks were on random users, typically infected through email attachments sent by small groups of criminals, demanding a few hundred dollars in cryptocurrency to unlock files typically a private individual's photographs and documents that the ransomware had encrypted. The Independent. |
| Bfgminer solo mining bitcoins | Ftm crypto price history |
| Crypto php virus | How to buy mtv crypto |
| Comprar bitcoins con tarjeta de debito | Bitcoin wiki mt gox bitcoins |
| How to use idex with metamask | 973 |
| Calculate bitocin priecs | 434 |
| Btc with segwit tps | American express bitcoin |
| Coin exhange | 443 |
| Biz why are the bankers so scared of crypto archive | He may have hidden some money using cryptocurrencies. Malware is designed to use just as much power as it needs, and it goes largely unnoticed. Crypto viruses come in a variety of forms, but here are the most significant email security threats to look out for when determining what email attack types you might be dealing with:. When encrypting files, the malware also deletes volume shadow copies and installs spyware that steals passwords and Bitcoin wallets. See also: New to Bitcoin? Young and Yung's original experimental cryptovirus had the victim send the asymmetric ciphertext to the attacker who deciphers it and returns the symmetric decryption key it contains to the victim for a fee. Symantec determined that these new variants, which it identified as CryptoLocker. |
| Convert amazon gift card to crypto | How.to sell on crypto.com |
Share: